Vitality knowledge has a key function in securing and defending our power future. As the worldwide shift to decentralized power networks retains rising, along with the rising adoption charges of electrical automobiles (EVs), cyber adversaries are discovering an increasing array of alternatives to assault and exploit the dynamic power sector.
By leveraging smart-grid power telemetry and smart-grid knowledge and fusing them into cybersecurity engines, operators may higher detect, forestall, and mitigate the newly rising cyber dangers and assaults earlier than any harm may very well be inflicted.
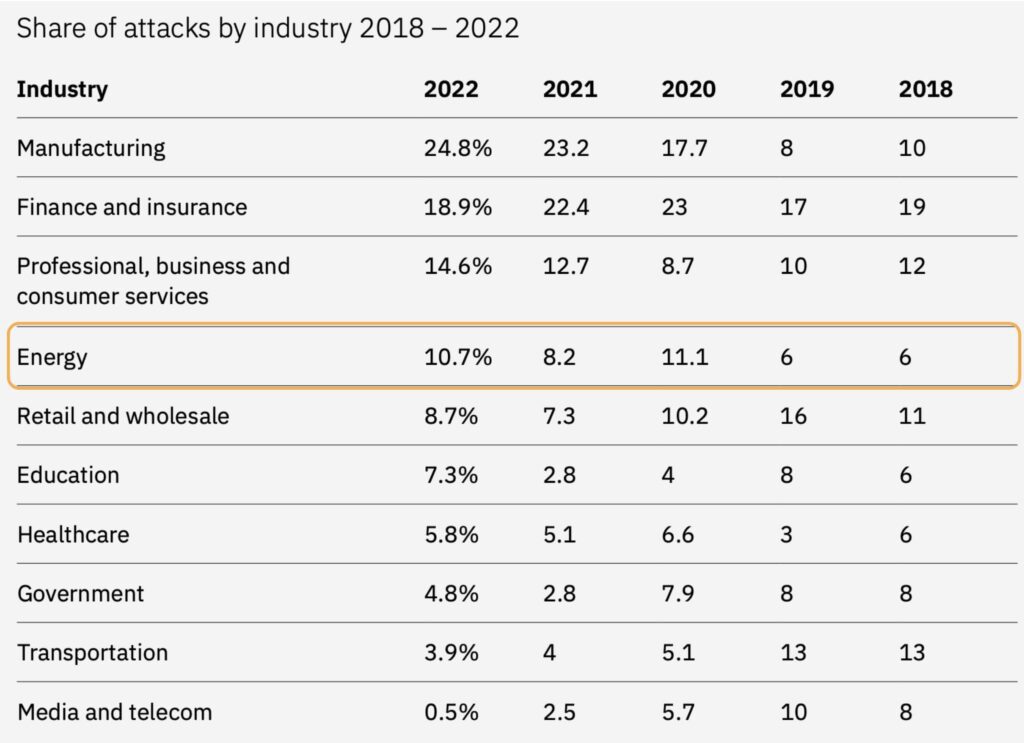
In accordance with the Risk Intelligence Index report, the power sector accounted for 10.7% of the
cyberattacks responded to by X-Drive in 2022, positioning power because the fourth-most focused business (Determine 1). In North America, power corporations skilled 20% of cyberattacks, making the power sector probably the most often focused business. Furthermore, the Russian invasion of Ukraine additional elevated issues over cyberattacks on power networks.
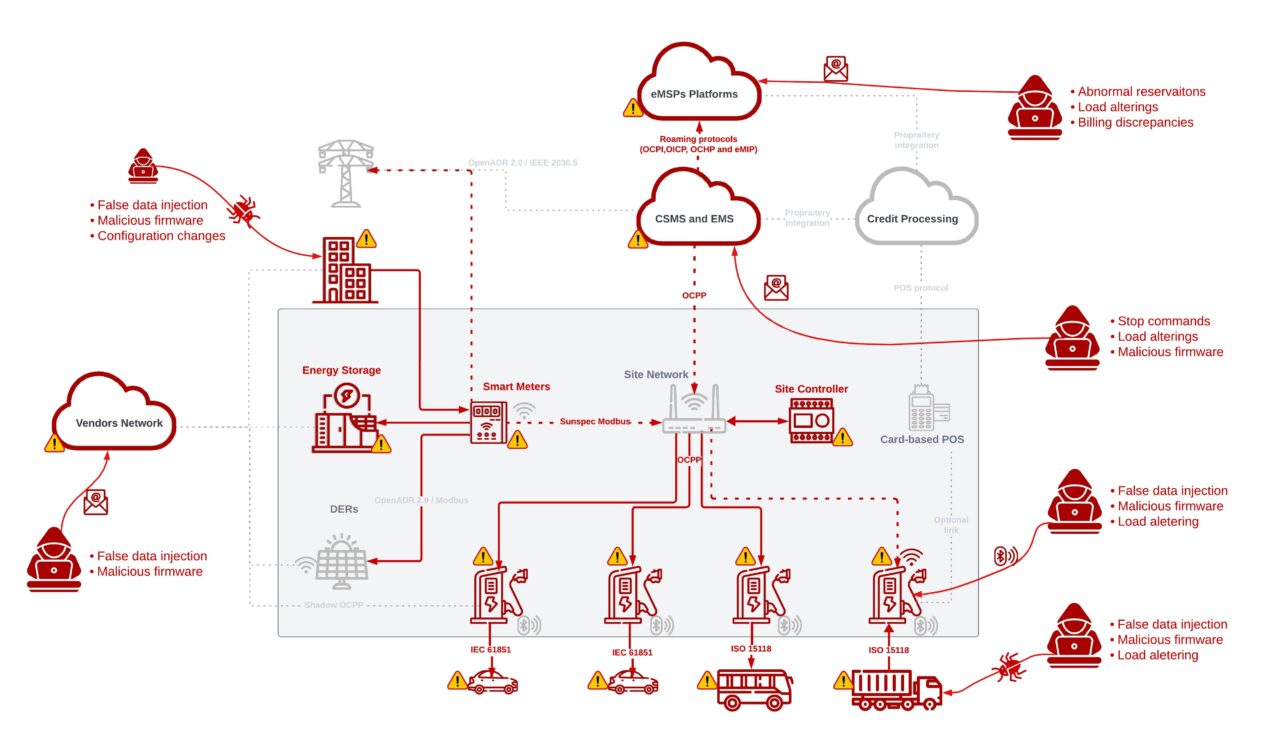
As new distributed power networks, corresponding to EV charging hubs (Determine 2), microgrids, substations, and distributed power sources corresponding to photo voltaic and wind, are getting extra digitally superior than ever earlier than, they’re changing into more and more difficult to defend, with versatile and huge assault surfaces.
In recent times, new platforms and elements, corresponding to power storage options, power administration methods, good meters, EV chargers, photo voltaic panels, and good inverters, have been launched to distributed power networks. Most of those elements are linked on to the Web or to the mobile community, together with to numerous cloud-based purposes, to streamline telemetry indicators and allow automated and distant
management over power manufacturing, distribution, and consumption.
Varied requirements and applied sciences have already been developed and built-in into immediately’s distributed power infrastructure such because the OCPP for good EV charging, IEC 61850 for digital substations, and IEEE 2030.5 for good power profile purposes. All make the most of the improvements of IoT (Web of Issues), cloud, and knowledge evaluation to enhance security, enhance productiveness and effectivity, improve income assortment, and help the unstable demand and manufacturing of the brand new power networks.
With increasingly linked methods to observe and safe, safety groups usually tend to miss one thing, enabling attackers to infiltrate and exploit the community, inflicting widespread harm to the power community and its customers. In consequence, we have to be sure that we’ve the proper safeguards in place, able to handle and face all of those dangers.
A distinct cybersecurity strategy is required in an effort to mitigate the newly emerged dangers with out forfeiting the advantages of digitization, automation, and data-driven optimizations of distributed power networks.
With this new array of methods, knowledge factors, administration protocols, and power telemetry indicators comes nice potential and alternative for cybersecurity. Safety groups may harness the brand new standardization and power knowledge factors to spice up their community safety with elevated visibility and superior correct detection to rapidly mitigate cyberattacks earlier than substantial harm might be inflicted.
Discovering Cyber Attackers’ Fingerprints in Vitality Networks
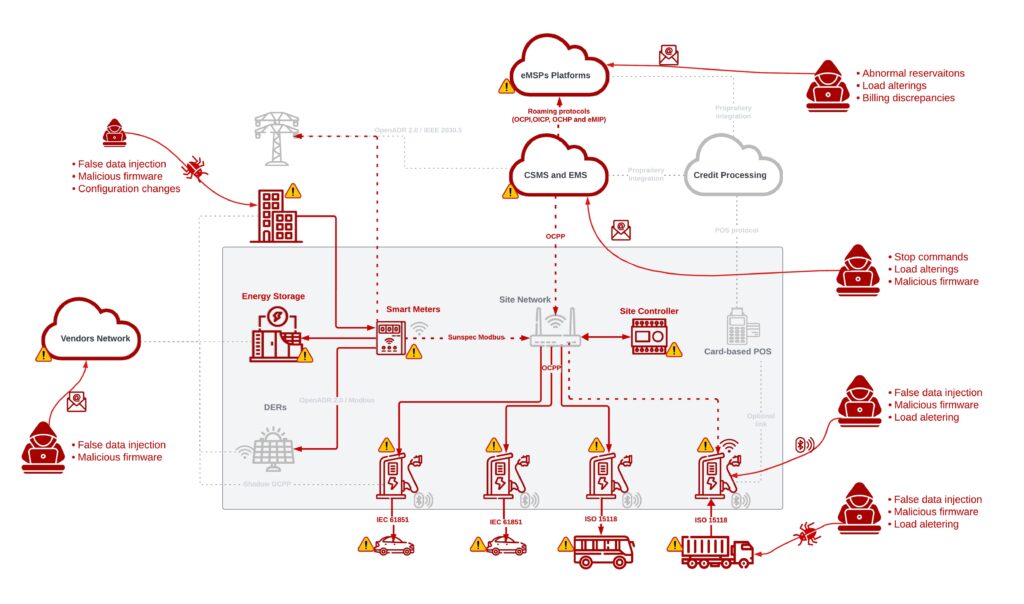
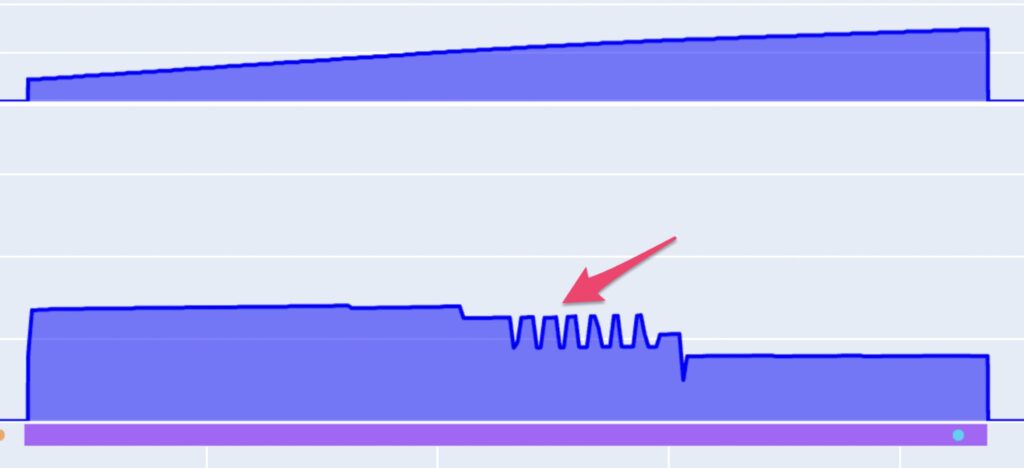
Most cybersecurity assaults on distributed power networks have energy-related signs and uncomfortable side effects. If not monitored and analyzed accurately, these power signs (Determine 3) may very well be skilled as mere upkeep points. A hacked good meter or inverter issuing false metering knowledge will often go unnoticed or undetected till it’s already too late. A spike in power as a consequence of power theft will likely be rendered as a upkeep challenge and so forth.
Cyber adversaries sometimes purpose to realize a selected aim or trigger a selected sort of injury through their assault. In distributed power networks, these cyberattacks may manifest in varied sorts of harm, together with native grid blackouts, {hardware} harm, power theft (within the case of EV charging), operational discontinuity (DoS/DDoS), native breakers tripping, and extra.
It’s essential to detect and reply to cyber incidents as quickly as attainable. By incorporating good grid and power telemetry along with demand response (DR) and administration protocols, new baselines may very well be supplied for distributed power networks. We may quickly and precisely detect anomalies and suspicious actions, and react to cyber assaults earlier than they start.
Fusing Vitality Telemetry With Cybersecurity
Does extra knowledge imply extra issues, and is there a necessity for a contextualized strategy? Whereas leveraging power knowledge for the sake of higher cybersecurity measures is necessary, the quantity of power knowledge factors being generated is immense. It may very well be a vicious cycle of introducing extra methods and elements that generate extra power knowledge. To make sense of all of it and allow data-driven actions, cybersecurity groups will should be geared up with the exact instruments and processes to reply measurably (minimizing false positives) and work together
with their counter operational groups in an efficient method.
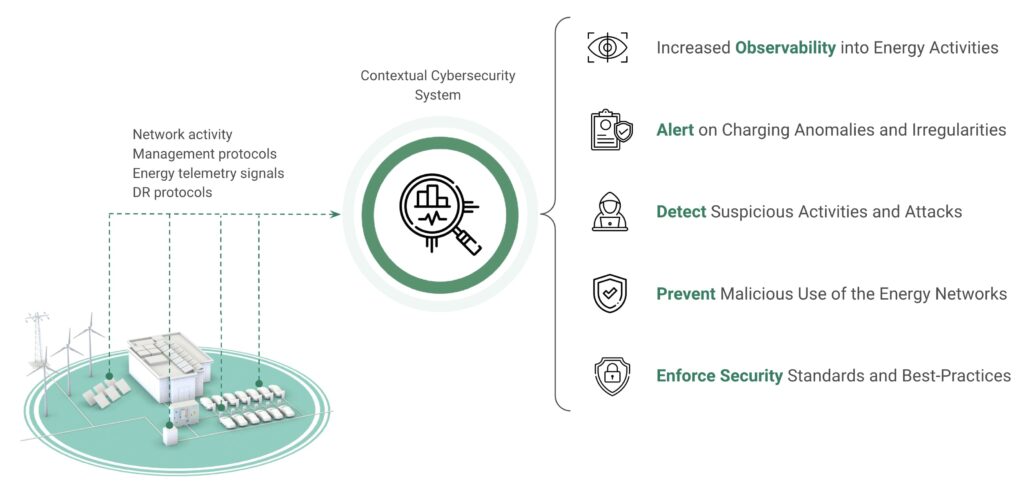
Generalistic cybersecurity options, whereas necessary, lack the wanted context, terminology, and know-how to detect energy-related signs of ongoing cyberattacks and will consequently enhance dramatically the false-positive alerts and even the false-negatives. That would trigger frustration and friction between the operational and cybersecurity groups. Furthermore, too many false-positive alerts may trigger alert fatigue, finally rendering these methods ineffective and exposing these networks to cyberattacks.
Integrating power telemetry with cybersecurity engines (Determine 4) underscores the necessity for tailor-made cybersecurity options within the power sector that incorporate and think about particular contextual elements and may quickly and successfully detect and reply to assaults and suspicious actions.
The Advantages of Contextualized Cybersecurity
By including context and power telemetry into cybersecurity methods and options, a number of
advantages emerge:
- Early menace detection: Contextualized cybersecurity can determine potential threats
early, permitting proactive mitigations as quickly as attainable, by integrating all power knowledge
factors with DR and administration protocols in the proper context. - Lowered false positives: With a deep understanding of the community and elements
operations, with their distinctive structure and protocols, a contextualized cybersecurity
system is not going to set off alerts on identified however hardly ever seen operations, and cut back the
likelihood of alert fatigue. - Improved compliance: Vitality corporations should adhere to a mess of laws
and requirements. Contextualized cybersecurity options may help meet compliance
necessities effectively and successfully and allow the wanted synergies between
operational and safety groups. - Improve utilization: Vitality corporations can allocate sources extra successfully by
prioritizing cybersecurity investments based mostly on the distinctive dangers they face. Contextualized cybersecurity measures bolster the resilience of power infrastructure towards focused assaults, decreasing downtime and guaranteeing a steady power provide.
The fusion of power telemetry with cybersecurity heralds a brand new period of contextualized safety within the power sector. To guard towards rising threats and make sure the continuity, availability, and safe operations of the distributed power networks and EV charging infrastructure, tailor-made contextualized cybersecurity options are now not a luxurious however a necessity. Because the power sector embraces this strategy, it may harness the advantages of data-driven effectivity with out compromising on safety, ushering in a brighter, safer future for the power panorama.
—Or Shwartz and Ron Tiberg-Shachar are co-founders and CPO and CEO, respectively, at SaiFlow, which offers a tailor-made cybersecurity resolution for CP, EVSE, DER, and distributed power networks, specializing in securing their customary protocols, corresponding to OCPP, OCPI, IEEE 2030.5, DNP3, IEC 61850, and extra. SaiFlow’s platform offers posture administration, cyber monitoring, detection, and prevention skills, all incorporating smart-grid and sensor knowledge in establishing the baselines, correlations, and anomalies of these kinds of networks.