An estimated 90% of software program merchandise used to handle the U.S. energy grid accommodates code “contributions” from Russian or Chinese language builders. The discovering from cyber threat administration answer agency Fortress Info Safety highlights new provide chain gaps and factors to a dire want for extra sturdy methods to safeguard towards insidious threats that lurk within the international software program provide chain, Alex Santos, co-founder and CEO of Fortress Info Safety, informed POWER.
The discovering stems from current analysis performed by Fortress, an organization that makes a speciality of crucial infrastructure provide chain safety. Beginning in 2022, the agency checked out roughly 900 sorts of software program utilized by energy firms, together with IT merchandise utilized for community administration, in addition to operational know-how (OT) merchandise, that are used to watch and management bodily processes and tools.
“This consists of merchandise from giant well-known distributors like feeder terminals, chromatographs, community switches, administration relays, and routers,” a Fortress report launched on Dec. 5 says. “The researchers pulled 392 information that used a number of complementary instruments for firmware and binary evaluation. From these information, they have been then in a position to create 224 Software program Payments of Supplies (SBOMs). They checked out largely open-source code.” it notes.
Of 7,918 elements Fortress reviewed, 13% had contributions from Russian and Chinese language builders. Nonetheless, the agency discovered that 90% of the merchandise used to handle the U.S. grid accommodates part contributions from builders that recognized as Russian or Chinese language. The researchers additionally discovered contributions from Cuba, Iran, and North Korea.
“To be clear, researchers solely counted elements with contributions as coming from Russia, China, or any nation if the creators acknowledged their nation of origin,” Fortress says. “Solely these builders who self-identified on a software program improvement platform as being from a rustic have been placed on that nation’s record. There isn’t any data on the platforms indicating that the code resulted from a state-sanctioned undertaking.” Whereas Fortress sees “a transparent correlation between the elevated vulnerabilities in some contributions and the nation of origin,” its specialists “can’t but set up if the nation of origin is the reason for the upper quantity,” the report acknowledges.
Nonetheless, the analysis means that software program with Russian or Chinese language-made code examined by Fortress analysis “is 2.25 occasions extra prone to have vulnerabilities,” the report notes. “Maybe much more troubling, that software program is thrice extra prone to have crucial vulnerabilities—the vulnerabilities which can be best to use and extra prone to enable harm to {hardware}.”
Lengthy-Standing Vulnerabilities
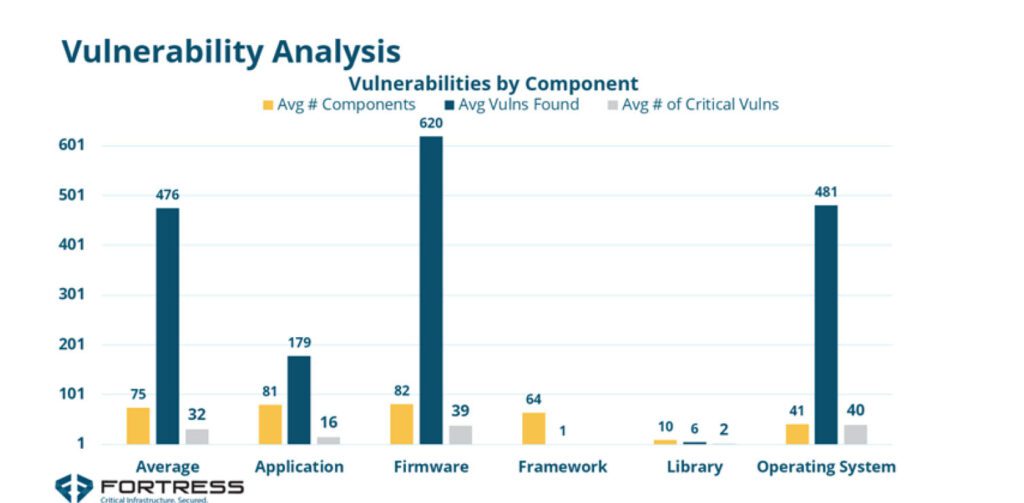
In keeping with the report, firmware—software program embedded instantly in {hardware} that gives low-level management for a tool’s particular {hardware}—reveals essentially the most vulnerabilities, with a median 620 vulnerabilities per product. “However working programs had simply as many crucial vulnerabilities—with 12% being crucial,” it notes. “In all, roughly 7% of all vulnerabilities have been crucial—the vulnerabilities that ought to be prioritized for remediation.”
In one other probably alarming discovering, the report means that vulnerabilities constructed into the software program operating crucial operations and elements don’t get fast consideration from distributors, suppliers, or utility suppliers. Whereas vulnerabilities are usually seven years outdated, the common age of crucial vulnerabilities is almost three years. In the meantime, solely 10% of elements are accountable for 92% of essentially the most crucial vulnerabilities, it suggests. “Two elements, glibc and linux_kernal, have been accountable for round 40% of those potential vulnerabilities.”
Fortress’s report arrives as actionable cybersecurity mitigation efforts are exhibiting a “decelerate” in comparison with momentum after the Log4J and SolarWinds crises, extremely refined nation-state assaults, greater than three years in the past. “These two, the assault and the vulnerability, drove plenty of cyber coverage from the chief department. However as a result of we’re people, we are inclined to neglect the disaster,” Santos mentioned.
Whereas rules have pushed IT departments to deal with software program safety, “nothing has occurred within the final couple of years,” he famous. “Now the stress is off, the regulators are slowing down, they’re feeling and succumbing to the stress of the software program producers,” he mentioned. “And the end-result is that our grid just isn’t as safe appropriately, on condition that we all know that our adversaries can use can conceal deep within the software program to to perpetrate their missions,” he mentioned. “We launched the report as a result of we have to preserve reminding those who it is a huge drawback.”
In keeping with Santos, a key answer could lay in pinpointing problematic elements. The agency has been adamant in its advocacy for common adoption of SBOMs as essentially the most environment friendly approach of shedding mild on vulnerabilities in a product. “In our analysis, we’ve proven that in the event you repair 10 elements—if we are able to repair these elements, make them safe, replace the software program that’s within the area—you’ll knock out 70% of vulnerabilities,” he mentioned. “That’s the most cost effective answer, but it surely’s nonetheless not low-cost, so it’s going to need to be an funding.”
Nonetheless, as well as, Fortress means that cybersecurity ought to be key procurement standards, although that may require extra certainty from the federal authorities. “America wants regulation of software program improvement platforms—both from business or from Washington,” it says.
SBOMs: A Software program ‘Ingredient Listing’
SBOMs are primarily an “IT record of components in software program,” Santos defined. “Software program just isn’t coded anymore—it’s assembled like Lego in blocks” from catalogs. Blocks, for instance, comprise a database or a login display screen, he mentioned. “So the SBOM is an ingredient record of the Lego items in our software program.”
The method of curating an “ingredient record” is complicated, given the numerous contributions to a software program product. Citing technological analysis and consulting agency Gartner, the report notes an estimated “40% to 80%” of strains in new software program undertaking code come from third events, similar to runtime, libraries, and part and software program improvement children.
The arrival of synthetic intelligence (AI), which automates software program constructing, is posing new challenges “to label and perceive what’s within the software program,” Santos mentioned. A fair greater threat, nevertheless, could also be posed by older software program variations, which can embrace obscure elements, he mentioned.
A key purpose that SBOMs have emerged as a vital cybersecurity mitigation effort is that that they’ll present transparency into what software program is made up of. SBOMs, notably, additionally helped safety groups monitor and mitigate harm from assaults, similar to from the 2020 SolarWinds assault and more moderen ransomware assaults in MOVEit software program purposes, Santos mentioned.
Nonetheless, organizations are struggling to implement SBOMs. In keeping with Gartner, solely 5% of organizations have adopted SBOMs, although it initiatives that by 2025, 60% of organizations could “mandate and standardize SBOMs” in software program engineering practices. In keeping with Fortress, “these numbers are nonetheless approach behind.” The agency notes: “It simply takes a backdoor, in a single firm, in a single crucial sector, to present unhealthy actors a gap into the programs operating crucial companies, like the ability grid.”
Within the energy area, “what’s blocking the earnest” to undertake SBOMs is two-fold, Santos steered. One is that “utilities at the moment are below huge price pressures,” he mentioned. On the identical time, software program builders have resisted SBOMs. Santos suggests this can be owing to price and legal responsibility issues. “My estimate is it’s $40 billion for distributors to repair the software program,” he mentioned.
Some utilities use software program that’s 10 years outdated, and that poses a round dilemma with questions on “whose job it’s to repair it,” he mentioned. “The outdated stuff remains to be there sitting susceptible, and producers refuse to repair it. So now, by default, it’s the utility’s drawback, but it surely’s actually exhausting for them to behave on it, as a result of you must get actually into the weeds of the software program, and it’s very expensive to do this.”
What’s Wanted: A Collaborative Effort for Extra Transparency
Within the U.S., federal entities just like the Cybersecurity & Infrastructure Safety Company (CISA) have supported SBOMs as a crucial device to forestall cyber assaults.The bipartisan Our on-line world Solarium Fee in 2020 urged the federal authorities to require SBOMs for software program it purchases, and in 2021, the White Home issued Govt Order 14028, which mandates authorities companies ought to have SBOMs for software program bought starting in 2024.
Nonetheless, business craves extra certainty, Fortress suggests. “Congress’s resolution in 2022 to take away language from the Nationwide Protection Authorization Act (NDAA) that may have required software program makers to incorporate an SBOM on merchandise provided to federal companies actually muddied the image,” it says.
Some progress is underway. On Aug. 10, CISA requested the open-source group for concepts on how one can safe code from their group. “The hope is to craft a report from these solutions that might come out later this 12 months,” Fortress notes.
CISA can be engaged on producing a “Safe Software program Self-Attestation Widespread Type for presidency distributors,” a doc that Fortress says would require software program producers supplying merchandise to the federal authorities to ensure the implementation of particular safety practices. The measure will imply that “software program makers will both have to vow the merchandise are being examined or have a particular timeline for testing to happen,” the agency explains.
Fortress suggests that after an inexpensive and sturdy commonplace is developed, all events can work with the federal government to plan “wise enforcement mechanisms.” It notes: “If the business takes steps to require SBOMs and Attestation kinds voluntarily, the much less the federal government should mandate them.”
Nonetheless, for now, private-sector collaborations and business options stay integral. “The software program improvement group would do us all an important service in the event that they joined the trouble to make sure code contributions on the platforms are safe. Particularly when these firms are attempting to keep away from a $40 billion-dollar tab,” the agency says.
“No person needs to create a scenario the place we’d like a software program business bailout, however we’d like the software program business to seek out options as an alternative of combating SBOM laws—which reportedly their lobbyists did earlier than the SBOM provision was pulled from the NDAA.”
—Sonal Patel is a POWER senior affiliate editor (@sonalcpatel, @POWERmagazine).